The Intriguing Lotus: A Deep Dive into Sagerunex

First post of the year — I wish you all a happy New Year. Habits die hard, so to inaugurate 2026, I have chosen to write about another (likely) China-linked APT.
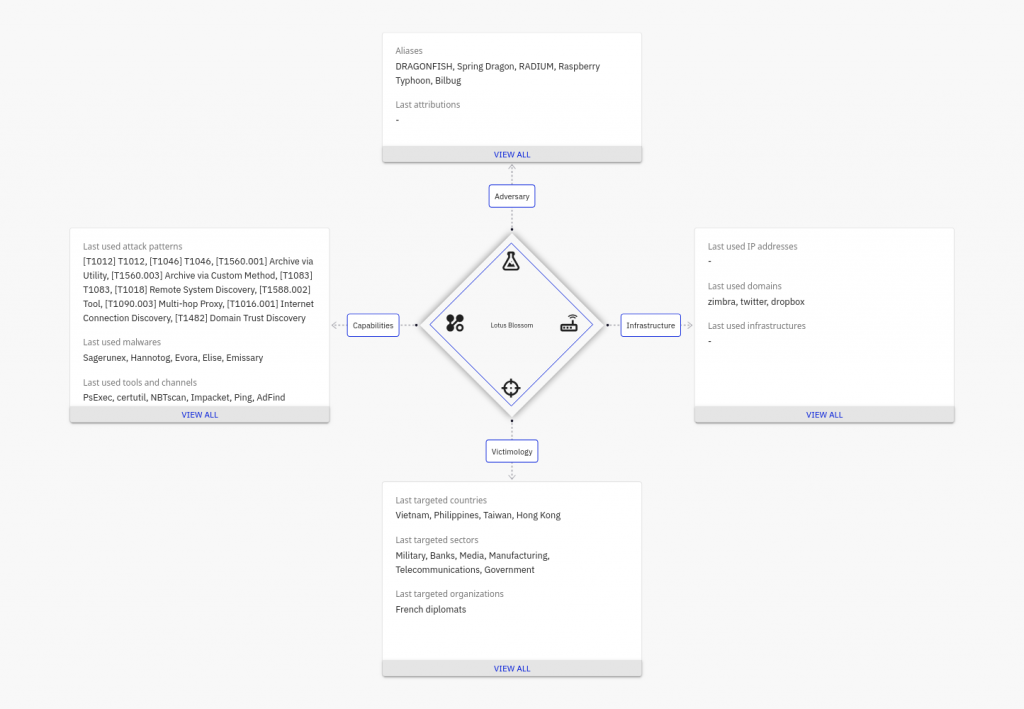
Lotus Blossom, also known as Red Salamander, Lotus Panda, or Billbug, is an intrusion set active since at least 2009. While several pieces of evidence suggest that this intrusion set is linked to China, it is worth noting that Lotus Panda does not appear to leverage the common shared tooling used among Chinese attackers, such as PlugX or ShadowPad.
In this post, I delve into one of Lotus Panda’s signature malware families, Sagerunex. While Symantec and Cisco Talos have already written about this piece of code, I felt like there were still some additional insights to share about it.
Victimology
Lotus Blossom is known to target the Southeast Asian region, including but not limited to Taiwan, Vietnam, the Philippines, Indonesia, and Hong Kong.
This intrusion set targets a wide range of sectors, including government organizations, telecommunications, manufacturing, as well as banking, energy, media, and the military. It has also targeted digital certificate issuers. As a result, the victimology associated with this intrusion set is quite broad.
In the past, it has also allegedly targeted French diplomats operating in this region. There is a reasonable probability that this was a case of tangential targeting, with these diplomats being targeted solely because of their presence in Southeast Asia. However, according to Symantec, this intrusion set also targeted communications, geospatial imaging, and defense sectors in the United States. According to Thales, this intrusion set also targeted France and Canada.
Analysts concur that the offensive operations of this intrusion set aim to collect intelligence.
Attribution
According to PwC, Lotus Panda (aka Red Salamander) is a “China-based threat actor”. CrowdStrike goes further, stating that it “is a targeted intrusion adversary with a suspected nexus to the People’s Republic of China (PRC).” For Symantec, Lotus Panda is a “China-linked group”.
Some editors even attribute Lotus Panda to the People’s Liberation Army, and more specifically to PLA Unit 78020. This attribution appears, however, to stem from a confusion between Lotus Blossom and Naikon. We do not find strong evidence in open sources suggesting that these represent either the same intrusion set or distinct subclusters of the latter.
That said, the victimology is fully consistent with a China-linked threat actor. Southeast Asian countries, as well as high-value and strategic sectors such as those targeted by Lotus Panda, are well-known priority targets for intrusion sets operating on behalf of the Chinese government.
Moreover, Symantec identified three computers in China being used to launch the Thrip attacks.
In a notable analysis, Viettel Intelligence also mentioned that this intrusion set appears to operate on UTC+8, further reinforcing the hypothesis that it may be a Chinese-backed intrusion set.
We therefore believe we a high level of confidence that this intrusion set is operating on behalf of China.
Now that we have a better understanding of Lotus Panda, let’s delve into the analysis of Sagerunex.
Malware Analysis
While Symantec and Cisco Talos did a great job analyzing Sagerunex, I thought that this piece of malware still kept some of its secrets. This is why I decided to spend some time working on it (sample hash:ddb767316a996b0a32bd72a49ab87ed243244e39).
As for the sample analyzed by Symantec, the one I investigated had no hardcoded configuration. Instead, the configuration is passed as an argument, and Sagerunex creates a file to store it on the computer on which it is running.
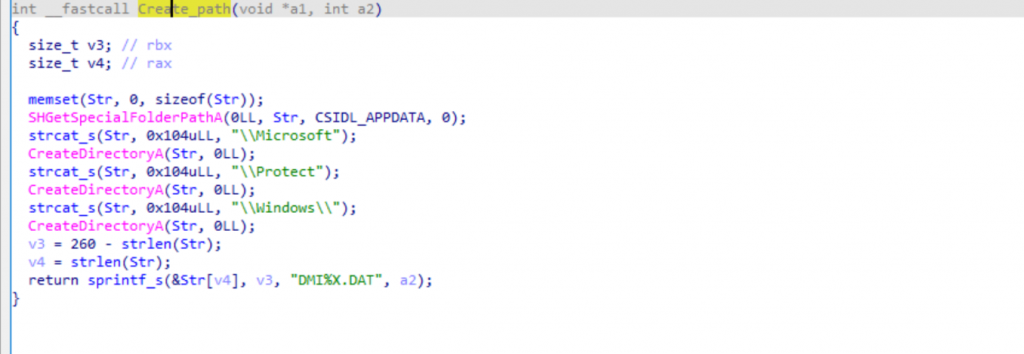
Figure: Creating the config file to be used by the malware
Main Features:
Sagerunex is shipped with several features, including modifying its configuration, executing commands remotely, downloading further files, or sending files to the C2.
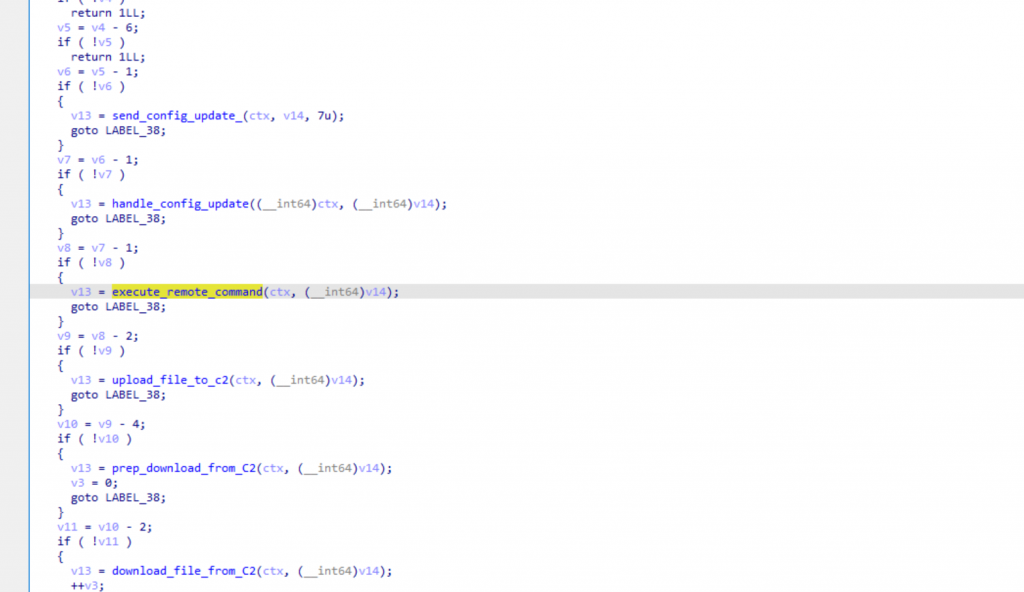
Figure: Features of Sagerunex
This piece of malware therefore appears as an efficient backdoor for espionage purposes.
When analyzing the commands supported by the malware, the sample shows that the attacker can execute executable files, DLLs, and arbitrary shell commands via cmd.exe.
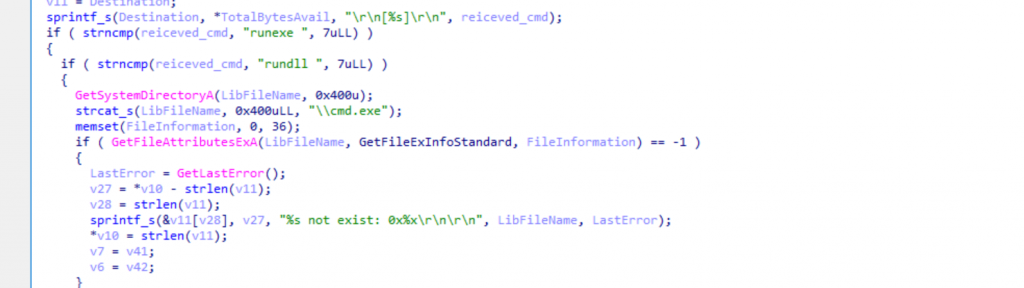
Figure: extract of the function used to execute files or command function
The malware inspects the command string received from the C2 server and determines the execution method based on its prefix:
- runexe : executes an .exe file
- rundll : loads a DLL and invokes a specified exported function
- any other command : is passed directly to cmd.exe for execution
By parsing these command prefixes, the malware allows the operator to flexibly execute programs, invoke DLL functions, or run arbitrary system commands on the infected host.
Communications:
To communicate with its command and control server (C2), Sagerunex uses the following user-agent:
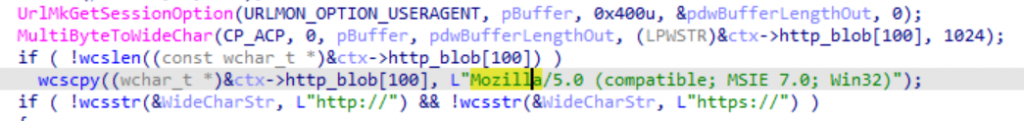
Figure: user-agent used by the malware
The malware uses WinHTTP for C2 communications. It initially attempts to connect using the system’s default WinHTTP configuration, which may result in a direct connection or the use of a configured proxy. If this attempt fails, it seems to fall back to multiple explicit proxy discovery mechanisms including WPAD, Internet Explorer, Firefox, auto-proxy, and preconfigured proxy settings.
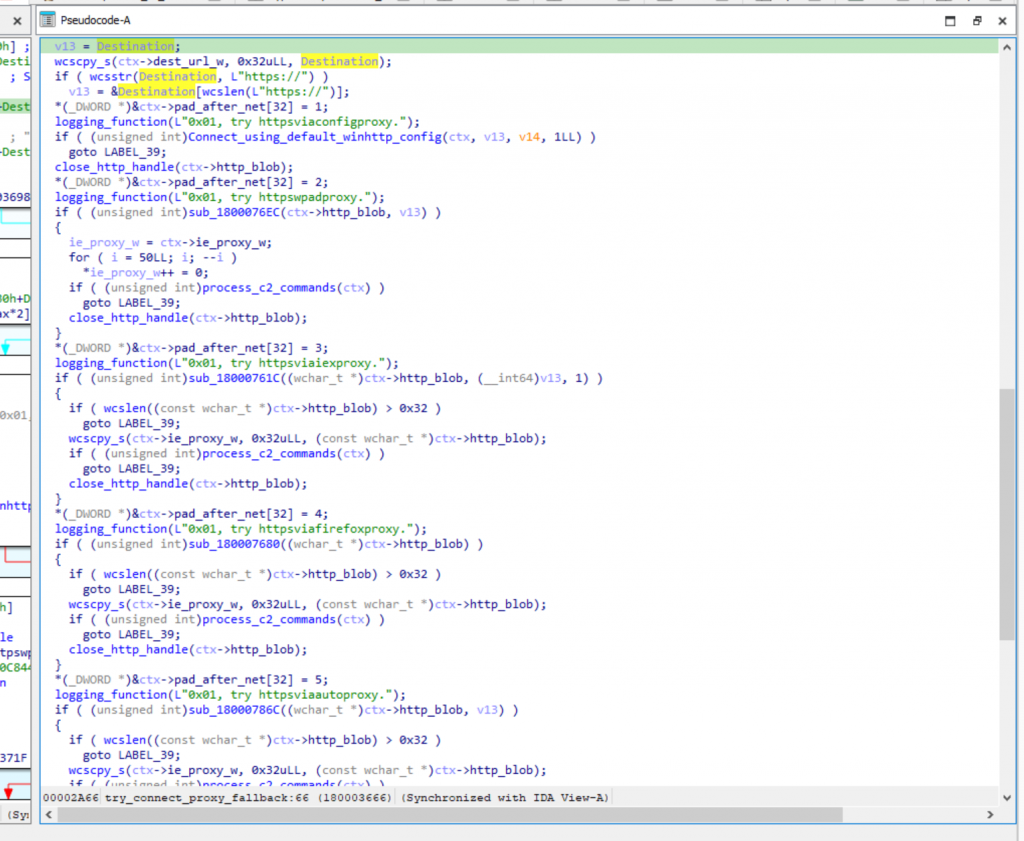
To get the default configuration on the infected machine, the malware attempts to open the registry key that may store the proxy configuration :
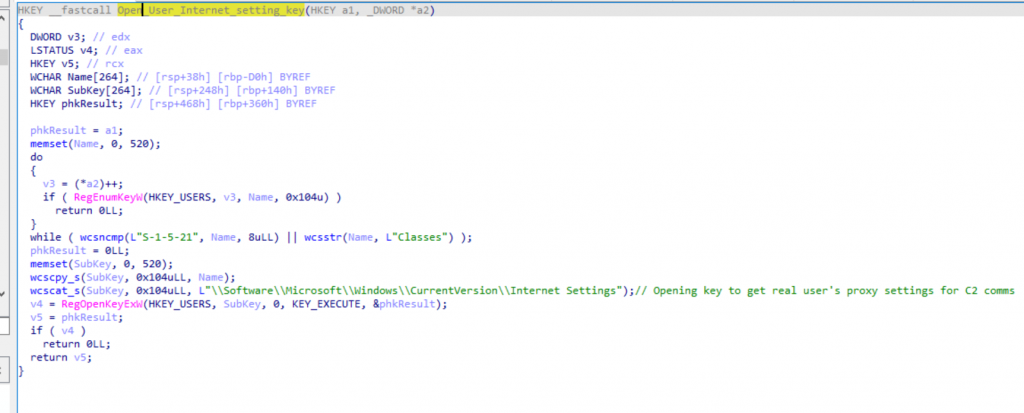
figure: Opening registry key to retrive proxy configuration
To fly under the radar when doing so, Sagerunex leverage Explorer token impersonation. It can then behave exactly like the logged-in user, ensuring proxy access, registry visibility, filesystem permissions, and reliable C2 communication, without spawning a new process:
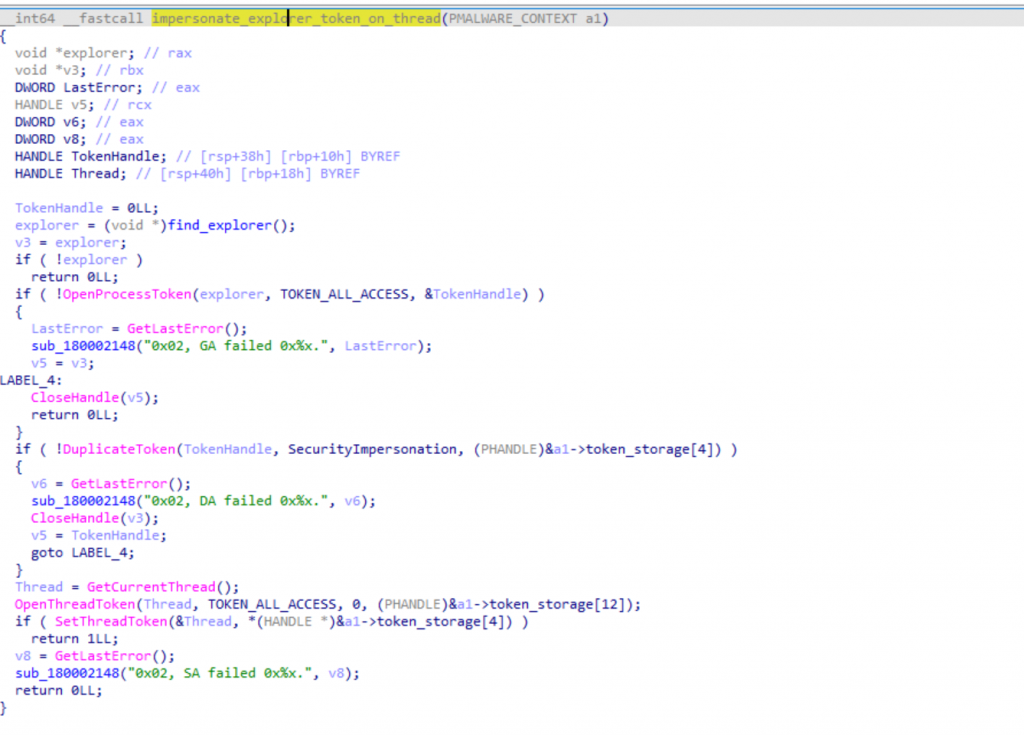
Figure: Sagerunex uses token impersonation to mimick Explorer.exe
Other:
To fly under the radar, it is also possible to set up operational time windows for Sagerunex and therefore have it operate only during office hours, as shown by the following function:
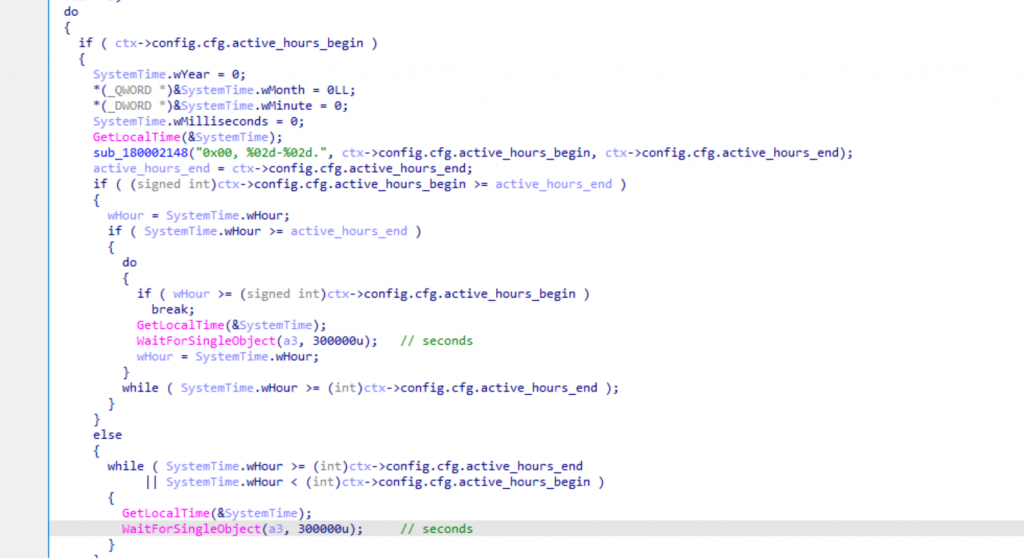
Figure: setting up time windows for the malware (I hope I was not too bad at recreating the custom structure used)
This strategy, coupled with token impersonation and the usage of proxies, shows that Lotus Panda actively attempts to avoid the detection of Sagerunex.
Conclusion:
It was definitely worth looking into Lotus Panda. The literature about this intrusion set is not only limited, but its signature malware, Sagerunex, is a very interesting piece of code. Highly efficient, this malware also attempts to stay as discreet as possible by leveraging several features, such as token impersonation, the use of default proxy configuration or configured proxies, and the configuration of custom operating time windows. Such an assessment is also consistent with Cisco Talos’ findings, according to which Sagerunex also leverages legitimate services such as Dropbox, Twitter, and Zimbra for C2 purposes.
